
FHE and blockchain – a perfect match
By Joseph Wilson, Head of Strategic Innovation at Optalysys
Take an in-depth look at how we can leverage blockchains in a way that ensures confidentiality, integrity, and availability.
Data is essential to nearly everything we do, yet effectively managing it remains a significant challenge. We must ensure it is safe, trustworthy, and usable, focusing on its: confidentiality, integrity, and availability. After all, information is only valuable if it can be used. Current security measures often strip away protections to evaluate data, placing confidentiality solely on trust. This reliance is risky, as vulnerabilities can be exploited by attackers, limiting the trust organisations can place in one another and therefore preventing the sharing of data.
Blockchain technology offers a promising solution, enabling the creation of secure, shared systems in a way that upholds confidentiality, integrity, and availability.
Blockchains
A blockchain is a way of creating a record or “ledger” of data.
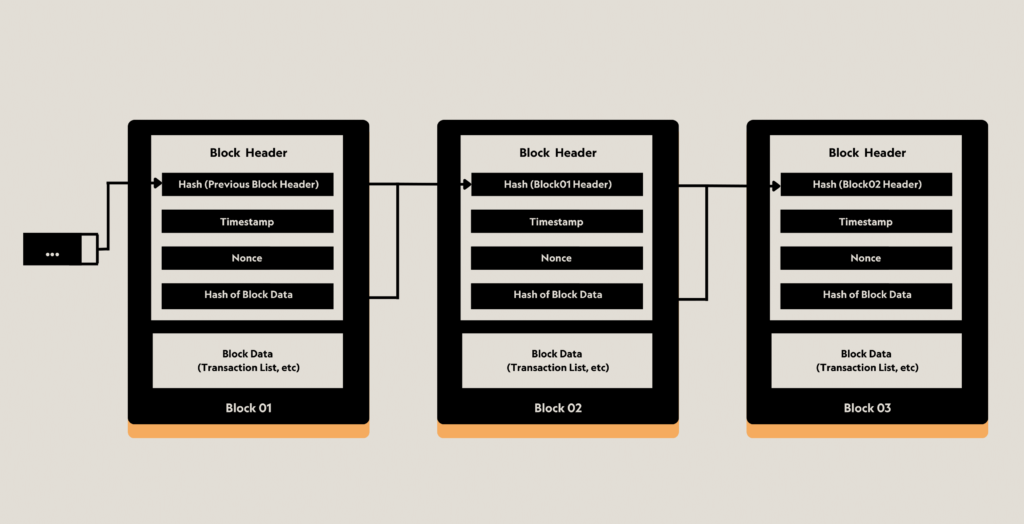
You can see that the data is inserted into each block. Each block is linked to subsequent blocks and is ‘locked in’ and immutable due to the way that blockchain is designed. If you’re unfamiliar with blockchain fundamentals, read our recent article “Blockchain and its security challenges” for a deeper dive into how blockchain works.
A Naive use of Blockchain
Let’s envision a hypothetical company that is looking to do identity verification. They need to collect your personal details, including full name, address, date of birth, passport details and social security identifiers. Once they have validated these details, they could store them on-chain along with evidence that these have been validated by our hypothetical company. That’s great to provide a reusable, validated identity artefact, but terrible for data privacy and confidentiality. We need a more nuanced approach. Similar challenges exist for B2B use cases e.g. supply chain validation – where specific relationships in a supply chain might give a competitive advantage (therefore provides a need for confidentiality).
We could suggest to these organisations that they encrypt the data before storing it on-chain. But now we have a different challenge…
Right now, wherever we want to compute over data, we must decrypt it first.
Even if we store information in an encrypted form in the blockchain, if someone else wants to use this information, then at some point we need to provide them with the means to decrypt it. That means we are back to the original problem of trust.
This means that many current implementations and applications of blockchain simply don’t implement access controls, and work only over applications where confidentiality is not an absolute requirement.
Scalability
In addition to the confidentiality problem, blockchains also face a problem of scaling. As more users are added to a blockchain, more data and more operations will follow. However, the ability of the supporting infrastructure and protocols to scale to this increased level of activity on the chain is not guaranteed. Throughput (and the associated cost of computing) has been a critical problem for many blockchain projects.
In conjunction with the challenges of confidentiality, this leads to what is known as the “Blockchain Trilemma” – the challenge of creating a blockchain that merges scalability, security and decentralisation.
As of late, a highly promising solution has been presented by so-called “Level 2” or L2 blockchains. This is a secondary layer of protocols built on top of an existing “L1” blockchain technology (such as Ethereum), allowing blockchains to be modular. This involves separating out tasks and processes that can be performed on the blockchain, performing them on separate “higher level” blockchains, with only the final output of these operations being reconciled to the L1 blockchain.
Suddenly, the overall throughput of blockchain is no longer limited by the performance of the protocol of the base chain – we can introduce principles of parallelism for scalability.
So how does this work? There are two mechanisms that enable this technical capability – smart contracts and rollups.
Smart contracts
Programs that are executed on the blockchain. When we say “on the blockchain”, that is quite literal – the key idea behind smart contracts is that the way blockchains work – and possess at any one moment a unique, irrevocable state – essentially allows the principles of state machines as a computing concept to be extended to the blockchain. Viewed as such, we can execute simple sequential programs (written in languages such as (Solidity) as pre-programmed transitions in the state of the blockchain. These programs are smart contracts.
Smart contracts allow us to specify a pre-set sequence of operations and conditions that must be met for the contract to execute, but separating the execution of these operations (which is required for scalability) from the main blockchain invites a new problem.
Once we perform transactions outside of the original blockchain, we also lose the proof of data integrity that comes with the cryptographic verification of sequential blocks. The question now is how we prove to the original blockchain that the sequence of operations performed on an L2 chain is valid and should be authorised.
Rollups
The answer is a rollup. This is a process by which operations performed outside of the primary blockchain can nonetheless be authenticated with respect to their correctness. Many off-chain transactions can be bundled (or “rolled up”) to the L1 blockchain in a single such operation, thus removing a significant amount of computational burden from the L1 chain. There are currently two types of rollup:
- Optimistic rollups: the validation is by user consensus that all the transactions were valid. This is enforced by a time period or “challenge window” during which participants in a smart contract can contest the validity of the outcome. This prevents malicious parties from authenticating the transactions they may have altered to the L1 blockchain. This naturally introduces a delay to L2 operations.
- Zero-knowledge proof (ZK) rollups: the cryptographic proofs of the correctness of the computation are used to attest to the validity of the state-change operations. This significantly compresses the information that needs to be recorded in the L1 blockchain, as (amongst other compression techniques) only the final state of the transactions needs to be recorded in the L1 chain. ZK rollups are also faster to execute, as there is no need for a challenge window.
So the smart contract specifies the data, blockchain states and other materials that are needed to execute a sequence of operations, while a rollup provides a mechanism for verifying the authenticity and correctness of the transaction sequence when operating outside of the main blockchain. Together, these solutions provide a solution for scalability, but what about confidentiality?
The problem is that the data involved in a smart contract is necessarily visible to the blockchain. This includes details such as the participants (or at least their respective wallet IDs), the data types and values, and the timing of the transactions. If we’re planning on bringing PII or company confidential information into the blockchain, we still need a solution.
Fully Homomorphic Encryption
We find one in Fully Homomorphic Encryption (FHE). FHE is a novel form of cryptography that allows us to perform computation in always-encrypted data. Under FHE, we can not only securely perform calculations over our own encrypted information, but over data held by multiple parties through techniques such as threshold MPC. In this way Smart Contracts are able to fully validate that a condition has been met so that it can execute, but without the exposure of confidential information being available on the ledger for all to access indefinitely. Essentially, FHE on Permissionless ledgers allows for closed access on a publicly available blockchain. Access control to sensitive data is mediated through access to encryption keys for eligible parties to engage in a publicly visible transaction on protected data.
FHE, then, is the tool that ultimately solves the problem of establishing much-needed confidentiality – as data can be protected throughout the entire lifecycle, including during processing, we no longer need to place our trust in the capacity of third parties to keep our data safe, while still allowing it to be used outside of our own systems.
While FHE has a dazzling range of applications in many different fields, when it comes to blockchain then this is the technology that brings together the confidentiality needed to protect sensitive data in the blockchain, and the computational capabilities needed to execute smart contracts. This provides a model of smart contracts in which only the relevant participants can see their own data, while still allowing for smart contracts to work.
Not only that, but FHE is also compatible with the ZK-rollup approach. Under this model, we now have a mechanism that allows for the use of permissionless blockchains as a shared storage, computation and execution framework for sensitive data.

A solution to the trilemma?
FHE and ZKP provide the missing utilities for confidentiality and scalability that will allow blockchains to reach the potential that was hinted at in previous eras of the technology, but which never quite reached the widespread adoption that was first predicted.
Where do things go once that blockchain trilemma has been solved? For the first time, this would represent at minimum a viable alternative to the current model of siloed, company-specific data stores.
However, confidentiality-enabled blockchains would be positioned to accomplish so much more. By positing a storage mechanism under which data is natively disaggregated and distributed while remaining secure throughout the associated data life-cycle, FHE-enabled blockchains could almost totally eliminate data duplication and siloing, allowing for industry-wide stores of information.
Let’s revisit our naive identity validation organisation we looked at earlier. Now they can provide validated identity information on-chain, allowing reuse. A verifier can ask ‘is this identity over 21’ and a confidential calculation can provide the answer without having to reveal the identity validated date of birth. This is a much more robust solution.
The incentive to minimise data access as enforced by the current flawed mechanisms for data protection would be replaced with an impetus to maximise the scope and availability of data in order to reap entirely new commercial opportunities.
Imagine a world in which seeking and acquiring new, high quality sources of data for decision making is as easy as using a search engine. Where data across complex supply chains can be rolled up into unified dashboards for every participant and end-consumer. Where identity and personal data management is no longer a tangled and opaque ecosystem of third parties, but instead controlled and orchestrated by the data holders themselves.
We’re not the first to notice this opportunity – as suggested above, FHE is seeing rapid adoption alongside the new wave of scalability approaches to blockchain, and many companies are now experimenting with implementations of FHE on the blockchain as a solution for the challenges identified in this article.
In some cases, that’s the organisations who provide FHE solutions that are compatible with blockchain – companies like Zama and Sunscreen provide tools and libraries for building encrypted smart contracts, while libraries such as OpenFHE are starting to provide functionality that is geared towards the blockchain ecosystem (such as the new Rust wrapper for OpenFHE).
In other cases, there are end-users developing applications based on FHE capabilities. This includes companies such as FHENIX and Mind Network.
Enabling scalability
Fully homomorphic encryption brings confidentiality to the blockchain, but this presents new challenges. While improvements to FHE at the cryptographic and algorithmic level have seen significant increases in encrypted processing speed, enabling the full potential of encrypted blockchain is contingent on the ability to perform large-scale FHE processing with low latency and lower costs.
That’s where hardware acceleration plays a major role. At Optalysys, we’re developing this hardware acceleration capability. Our Explore cloud platform is our solution for demonstrating the technology that we’re building, enabling users to connect to and evaluate our early FHE accelerators as we continue to develop a high-speed high-scalability solution. The encrypted blockchain space represents an exciting opportunity to drive the field of FHE forwards, and we are ready to assist in the delivery of POCs and partnerships with interested organisations, developers and entrepreneurs.

